“NOTE: Vocab
RFID Reader - The box-like object that can be activated by an RFID tagRFID Tag/RFID Card - The card or tag that activates the reader. I took apart one and is displayed in the pictures above. RFID System - The tag and the reader work together.Electromagnetic Waves - A wave that contains both electric and magnetic waves that are traveling on the same frequency and are perpendicular to each other.EMC - Electromagnetic current.EMC Shielding - blocks, reflects, and/or absorbs an electromagnetic current.
This is an RFID blocking experiment where you test out multiple ways to protect your RFID credentials. RFID is everywhere these days, it’s in credit cards and phones for the tap to pay like Apple Pay and Google Pay. However, it is most commonly used by hotels, businesses, and schools as access cards. All you do is wave your card in front of the reader and it lets you in.
Nowadays, there is a lot of fear about RFID hackers stealing your credit card information through RFID readers. In reality, no scammers even bother to steal your information with RFID scanners. In order to steal information this way, they would need a very high-powered reader (which is very expensive) and need to be in an area where a lot of people use RFID credit cards (there aren’t that many). Additionally, credit cards are encrypted, so the scammer would need to acquire the information through this difficult process and then decrypt it. There are a lot of cheaper and easier ways to get credit card information online. Instead, most RFID is stealing credentials rather than credit cards. If a high-security place like a government building, a bank, or a different building used RFID people become more interested in stealing cards. This project is going to focus more on protecting these credential cards rather than credit cards.
note: This introduction is going to be kind of an infodump so you can understand how the project works, so I recommend at least skimming through the sections below.
Background Information
Before we start this project it’s important to understand how RFID works. This is a really basic explanation of how RFID works, so if you want to go into more detail I suggest reading this article. I included a lot of the information you see here in
Basically, the reader sends out an electromagnetic field that the RFID card picks up, which triggers the card to send digital information back to the reader through radio waves. There are a couple of variations to this process that depends on the card, such as:
Active RFID Tags - There is a battery in the card that gives it the power to send information to the reader. These do better in longer distances and are bulkier than passive tags.Passive RFID Tags - All of the energy the card needs is harvested from the reader through the electromagnetic field. Most hotel keys are passive, which is why they are smaller and need to be right next to the reader.In addition to having different energy methods, RFID systems can run at different radio frequencies, such as:
125 kHz or Low Frequency (LF) - The oldest frequency, but also the cheapest. This frequency is one of the most documented, which makes information on how to break in widely available. It also has no government regulations.13.56 MHz or High Frequency (HF) - Newer than LF and more secure. It can be more expensive, but not by much. It is also the most commonly used and found in most hotel cards.Ultra-High Frequency (UHF) 865868 MHz (Europe) or 902928 MHz (North America) - These tags are most often used by trucking and railroad companies to keep track of trucks and their inventory. These are used less because they have more regulations than other kinds. UHF tends to interfere with other systems as well.There are some other kinds, but these are the most common. For this project we’re using HF or 13.56 MHz as that is the cheapest and most common.
Where Can We Find RFID in our Lives?
Hotel keys tend to be the most common. Not every hotel uses RFID, but you can find a lot in a city.Apple Pay/Google Pay uses a special kind of RFID called NFC (near field communication) to communicate with the reader.EZ-Pay or other automatic toll booth payments use RFID to track who is coming through and bill their account.Pets are often injected with an RFID microchip to keep track of their medical records and help identify lost animals.Schools and businesses have also been picking up RFID recently, to keep track of who is coming in and out, and to keep people out who aren’t supposed to be there.If you think this project is cool, wait until you hear about RFID implants. These are implanted usually into a human hand and can be programmed to open doors, tap to pay, send a website link to someone’s phone, and a whole lot of other super cool stuff!
There is no limit to the awesome stuff that RFID can do, so let’s get started!
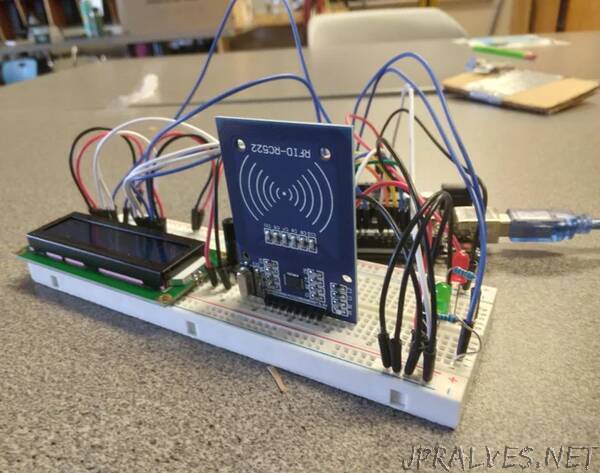
Supplies
- Arduino Uno
- Computer for programming
- RFID rc522 module (should come with 2 tags, but in my package one was broken so be prepared.)
- LCD1602 module (an i2c can work as well, but you might have to change my code a bit)
- lots of male-male wires.
- Breadboard
- Potentiometer 10K
- Red and green LED
- two 10K resistors
- Aluminum foil
- Duct tape
- An RFID blocking wallet (below are the two I used, but I recommend experimenting with your own!)
- Buffway
- ID Stronghold (highly recommended)
Optional
- A servo
- You can build a fake door out of cardboard and wood that can open as a demonstration.
- collected hotel cards (keep in mind that the rc522 is a high frequency operating reader, so it won’t respond to low-frequency tags)
- A regular non-RFID blocking wallet”
