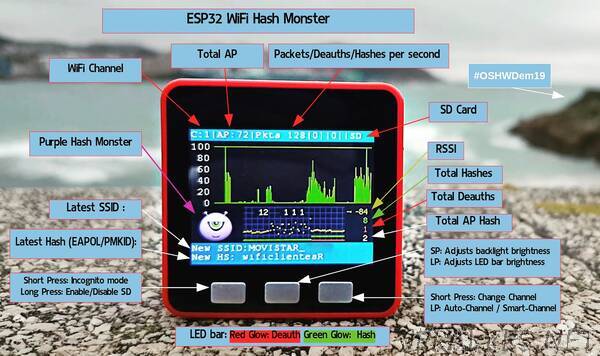
“WiFi Hash Purple Monster, store EAPOL & PMKID packets in an SD CARD using a M5STACK / ESP32 device.
90% of the code is based on the great PacketMonitor32 from follow on Twitter and the port to M5Stack from macsbug. It was a challenge to see if I could mimic the operation of pwnagotchi follow on Twitter in an ESP32 SoC.
When a wifi device connect to an AP with WPA2/PSK instead of sharing the wifi key they exchange 4 EAPOL messages, this method is known as the 4-way handshake, capturing these 4 packets is possible to guess the password using dictonary attacks or brute force attack, recentely there is a more efficent way to calculate the wifi key using just one PMKID packet.
Purple Hash Monster capture all the EAPOL / PMKID packets on the SD Card for further analysis.
Short press on first button will change the WiFi channel, long press will enable the SD Card and all EAPOL / PMKID will be stored on the SD-Card.
Short press on the third button will change the backlight brightness, long press will change the brigness of the LED bar.
When a deauth packet is detected left LED bar will became red and for every EAPOL / PMKID detected right LED bar will became green, also de Purple Hash Monster behaviour will change depending on the WiFi trafic and packets detected.”
