“Device configuration from the cloud with TLS1.3 security
Story
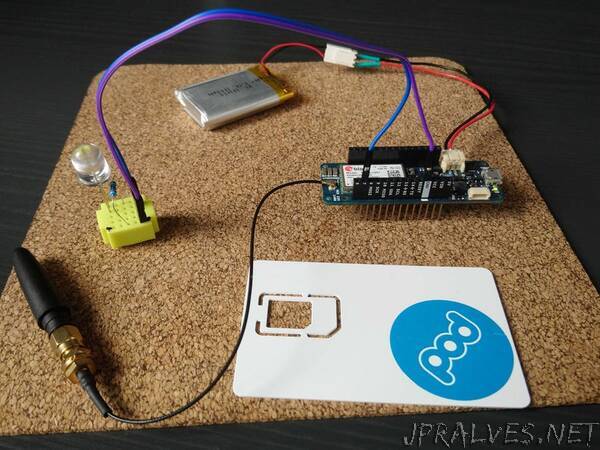
The project is intended to demonstrate Pod IoT security solution – SAFE2 applet which may be used to obtain securely and in the authenticated way the configuration data from a cloud server.
The SAFE2 applet is based on the expansion of the GSMA IoT SAFE idea. The applet is intended for the simplest and constrained IoT devices to provide bi-directional secure data exchange with a server.
The solution is suitable to improve communication security level of already deployed projects, where the free hardware resources are not available to implement cryptographic protocols.
SAFE2
The SAFE2 applet in the SIM contains an implementation of the TLS1.3 protocol in Pre Shared Key mode. The SIM not only contains the protocols logic but also stores the unique Pre Shared Key (PSK). The SIM is able to proceed PSK updates via OTA commands in secure manner.
The SIM stores an url, endpoint and port number to access the server (IoT platform).
The SIM is responsible for all the protocol steps including domain name resolving and for repeating attempts until the request will be delivered to the server.
To get configuration data from a server via SAFE2 applet, the Device Application shall send specific commands to the SIM by means of Modem Middleware - AT commands for generic SIM access, namely “AT+CSIM”.
First of all the supplementary logical channel must be open (to not interfere with the GSM session between the modem and the SIM in the base channel). Then the applet must be selected in the new logical channel and a specific command shall be send to the applet to initiate the HTTP GET request to the server. Each GET request contains the ICCID of the SIM (unique identifier of the SIM card) and the DeviceID which shall be provided by the Device Application in advance. The SIM will establish TLS 1.3 session and pass the request in encrypted and authenticated way to the proxy. The proxy will forward the request from the SIM to the server and the response from the server to the SIM. The Device Application shall poll the status of the request and collect the data when they will be available. The supplementary logical channel shall be closed at the end for reuse.
Configuration data
The configuration data shall be setup by means of Luner IoT Suite.
To create configuration the access token shall be obtained via the credentials provided.
Device ID is the unique identifier of the Arduino MKR GSM 1400 board. The scetch contains the code to extract Device ID and provide it to the SAFE2 applet.
The ICCID is the unique identifier of the SIM card used.
The “Body” contains the configuration which will be delivered in clear to the device from the SIM. The Body shall be less than 255 characters.
The Device Application shall be able to parse the configuration data provided.”
