“Update to Federal Information Processing Standard aims to help companies get products to market faster.
Electronic device manufacturers should find it less time-consuming to bring their wares to both the U.S. and international markets as a result of new requirements issued by the National Institute of Standards and Technology (NIST), which has updated the Federal Information Processing Standard (FIPS) for testing the effectiveness of a device’s data encryption.
Virtually all devices that receive and process electronic data—hardware used in laptops and cell phones as well as software that also exchanges information through networks—use some form of encryption to protect this data from prying eyes. FIPS 140-3: Security Requirements for Cryptographic Modules specifies the requirements a device’s encryption system must meet if it is to be used by the federal government. The standard affects the broader IT market because of the number of other organizations that interact with the government.
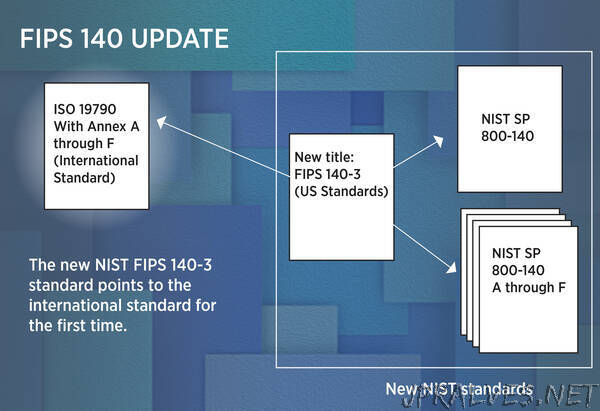
Announced today on the Federal Register, the newly released FIPS 140-3 modernizes the standard and essentially makes the U.S. standard a “pointer” indicating that manufacturers should now use the international standard, which NIST helped to develop.
Any product that adheres to the international standard—known as ISO 19790—will therefore use an encryption approach that is acceptable both within and outside the United States. This should streamline a manufacturer’s process for bringing a device to market because it reduces redundancy for companies trying to sell products internationally.
“Technology changes rapidly,” said NIST computer scientist Mike Cooper. “Testing takes a long time and every day a company spends on it is a day its product is not on the market. We want to minimize that, because there’s a limited time window before a product becomes obsolete.”
Like previous FIPS 140 versions, the first of which was created in 1982, FIPS 140-3 will be used primarily by laboratories that test new products’ encryption algorithms. Its influence, however, will be far wider.
Companies that wish to sell their goods abroad have had to put their devices through further testing regimes to satisfy other countries, but the update eliminates that need, Cooper said.
“For large manufacturers, this allows them to say that they’ve proved their cryptography in many countries at once,” he said. “It also allows for transfer of test results across borders. It gives us a better way to accept test results since they’ve been tested according to the same standard.”
The change also will help companies resolve a nagging dilemma: remaining in compliance with industry standards while also updating their products to address security vulnerabilities that sometimes turn up.
“Before this update, if we discovered a vulnerability or added a feature we’d need to go through an entire recertification round. That takes months, but our software development lifecycles are far shorter than that,” said Dominic Rizzo, who is the technical lead on Google’s Titan Security Key, a product that helps protect the supply chain. “With this change, the benefit to the government is they will get our best work faster.”
Because countries use varied encryption approaches, NIST is also creating a set of six other publications that list the algorithms that are approved for use within the U.S. These are NIST Special Publication (SP) 800-140 Volumes A-F, which function as an appendix to FIPS 140, and will be available at a later date. The SP volumes list what are essentially a subset of the algorithms that meet the ISO standard.
“These algorithms match up subject for subject with the ISO document,” Cooper said. “Putting them in this appendix allows the U.S. to adopt the ISO standard but still retain some control over what we allow.”
Cooper also said that NIST would be introducing an automated service to speed validation further. For the last step in the validation process, testing labs need to submit the results of a given device’s performance to NIST, and NIST employees have had to check to make sure the results contain the correct data. The new automated cryptography validation protocol (ACVP) will be able to perform this step automatically.
“If a lab submits the results in the right format and all the required data is present, our server will be able to approve the validation,” Cooper said. “We plan to have ACVP ready in April of this year.””
