Other
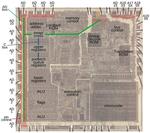
“The Intel 8086 microprocessor (1978) started the x86 architecture that continues to this day. In this blog post, I’m focusing on a small part of the chip: the address and data pins that connect the chip to external memory …

“This is a Noname graphical LCD display salvaged from an unknown device. We are going to figure out its pinout and try to interface it. Introduction I am basically writing this tutorial as a note for myself to avoid another …

“A key component of any processor is instruction decoding: analyzing a numeric opcode and figuring out what actions need to be taken. The Intel 8086 processor (1978) has a complex instruction set, making instruction decoding a challenge. The first step …

“While programmers today take division for granted, most microprocessors in the 1970s could only add and subtract — division required a slow and tedious loop implemented in assembly code. One of the nice features of the Intel 8086 processor (1978) was …

“Intel introduced the 8086 microprocessor in 1978. This processor ended up being hugely influential, setting the path for the x86 architecture that is extensively used today. One interesting feature of the 8086 was instructions that can efficiently operate on blocks …

“Like most processors, the Intel 8086 (1978) provides registers that are faster than main memory. As well as the registers that are visible to the programmer, the 8086 has a handful of internal registers that are hidden from the user …

“The Intel 8086 processor (1978) has a complicated instruction set with instructions ranging from one to six bytes long. This raises the question of how the processor knows the length of an instruction.1 The answer is that the 8086 …

“One interesting aspect of a computer’s instruction set is its addressing modes, how the computer determines the address for a memory access. The Intel 8086 (1978) used the ModR/M byte, a special byte following the opcode, to select …

“Interrupts have been an important part of computers since the mid-1950s,1 providing a mechanism to interrupt a program’s execution. Interrupts allows the computer to handle time-critical tasks such as I/O device operations. In this blog post, I …
“Status flags are a key part of most processors, indicating if an arithmetic result is negative, zero, or has a carry, for instance. In this post, I take a close look at the flag circuitry in the Intel 8086 processor …
